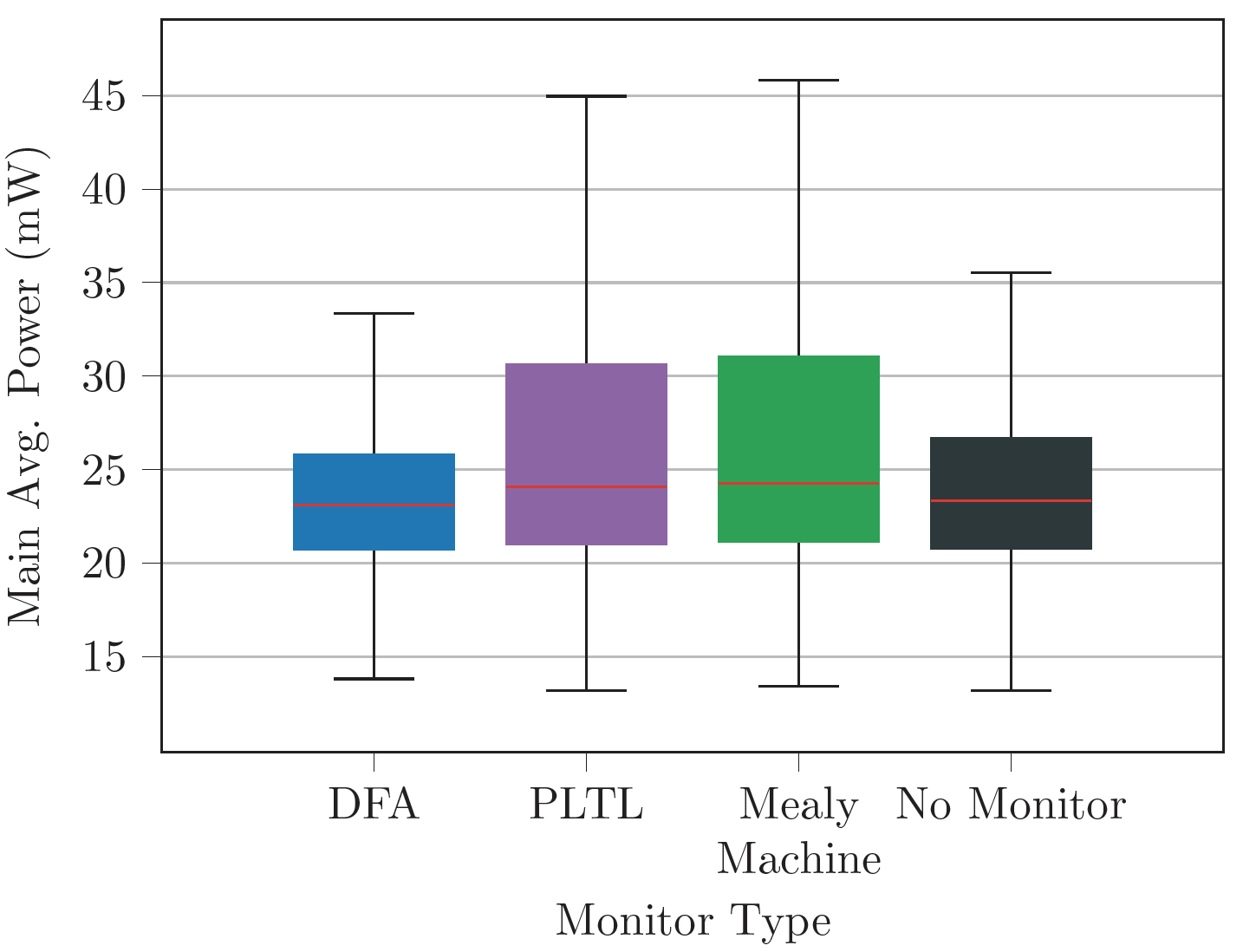
Implementation
Following are the two ways Phoenix can be deployed:
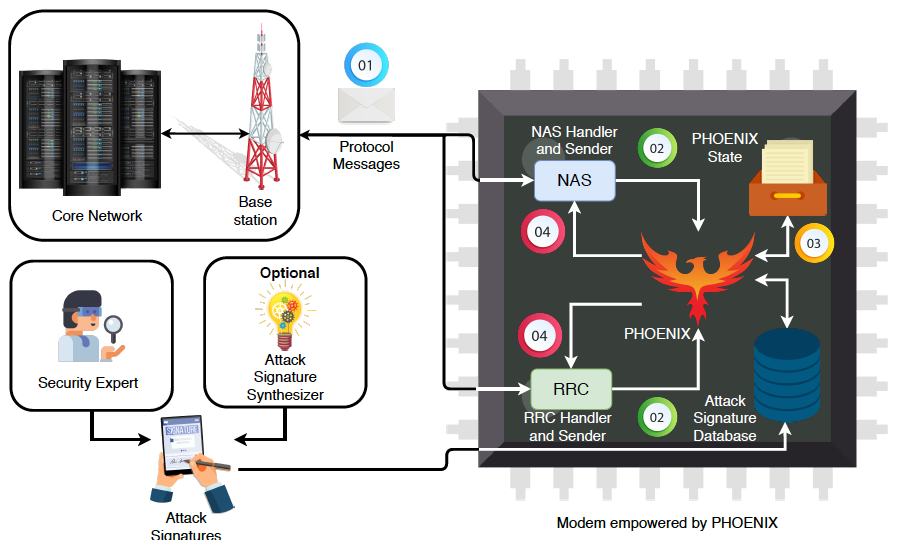
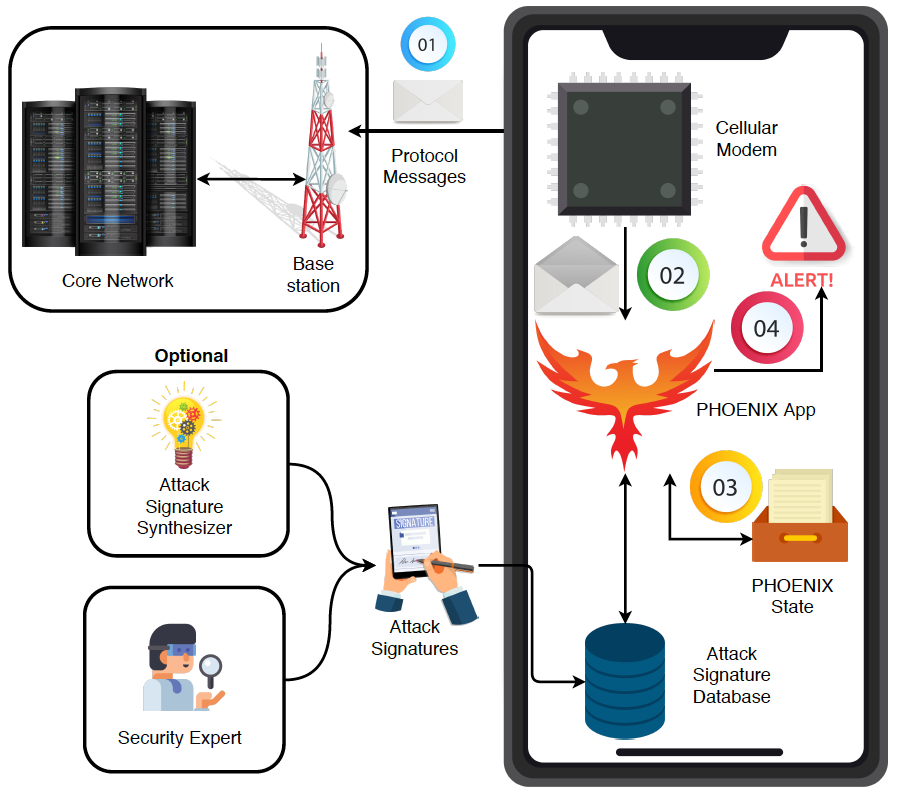
Following are the key components that constitute Phoenix (deployed as an android app)
Message Extractor
Firstly the message extractor reads events from the baseband processor. We used MobileInsight's dissector to efficiently capture traffic of NAS and RRC Layers. We then apply required propositions and forward the message to the monitor.
Monitor Component
We implemented our own monitors using Python For Android since MobileInsight is written in Python. Now let's discuss implementation of each monitor against attack signatures.
- DFA: DFA monitors the set of transitions, list of accepting states, current state and the alphabet in memory. If transitions lands on a non-accepting state it is considered an attack.
- MM: Mealy Machine monitors are similar to DFA but since it doesn't have any accepting and non-accepting states, so the output symbol of the transition indicates which particular attack has occured.
- PLTL: We used dynamic programming to monitor PLTL formulas. The monitor stores a single bit for each sub-formulas truth value and uses bitwise operations to identify truth values.